Welcome back my social engineers/hackarians! Today we'll be looking

into a fantastic piece of software, The Social-Engineer Toolkit or just SET for short. SET is designed, Developed and used by several Social-engineers. So... Let's get started!
Getting Familiar
When you boot up SET you'll see this screen:
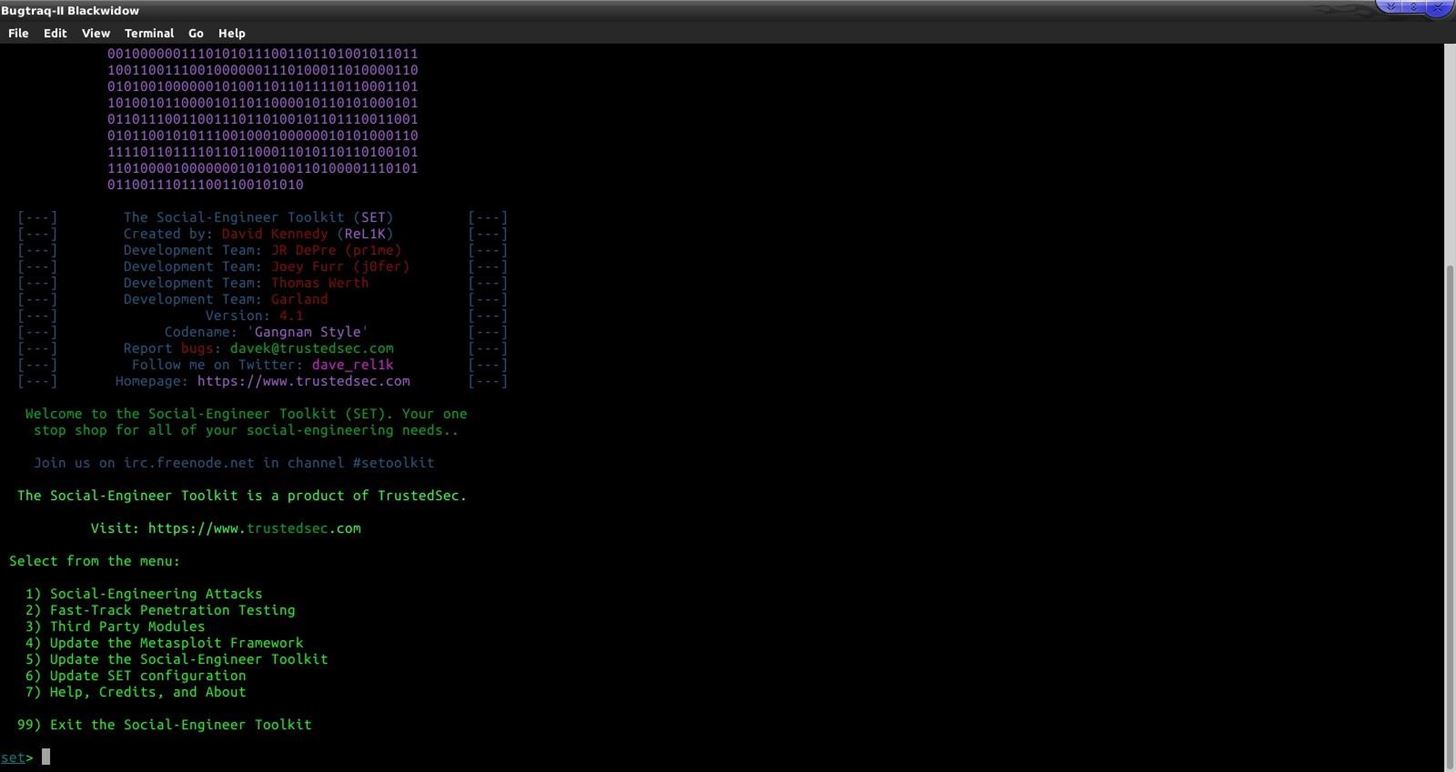
Now we are able to pick one of the options listed above
We'll use:
>1) Social engineering attacks
>2) Fast-track penetration testing
The other options are not important. So what happens when we press 1 We'll get this screen:
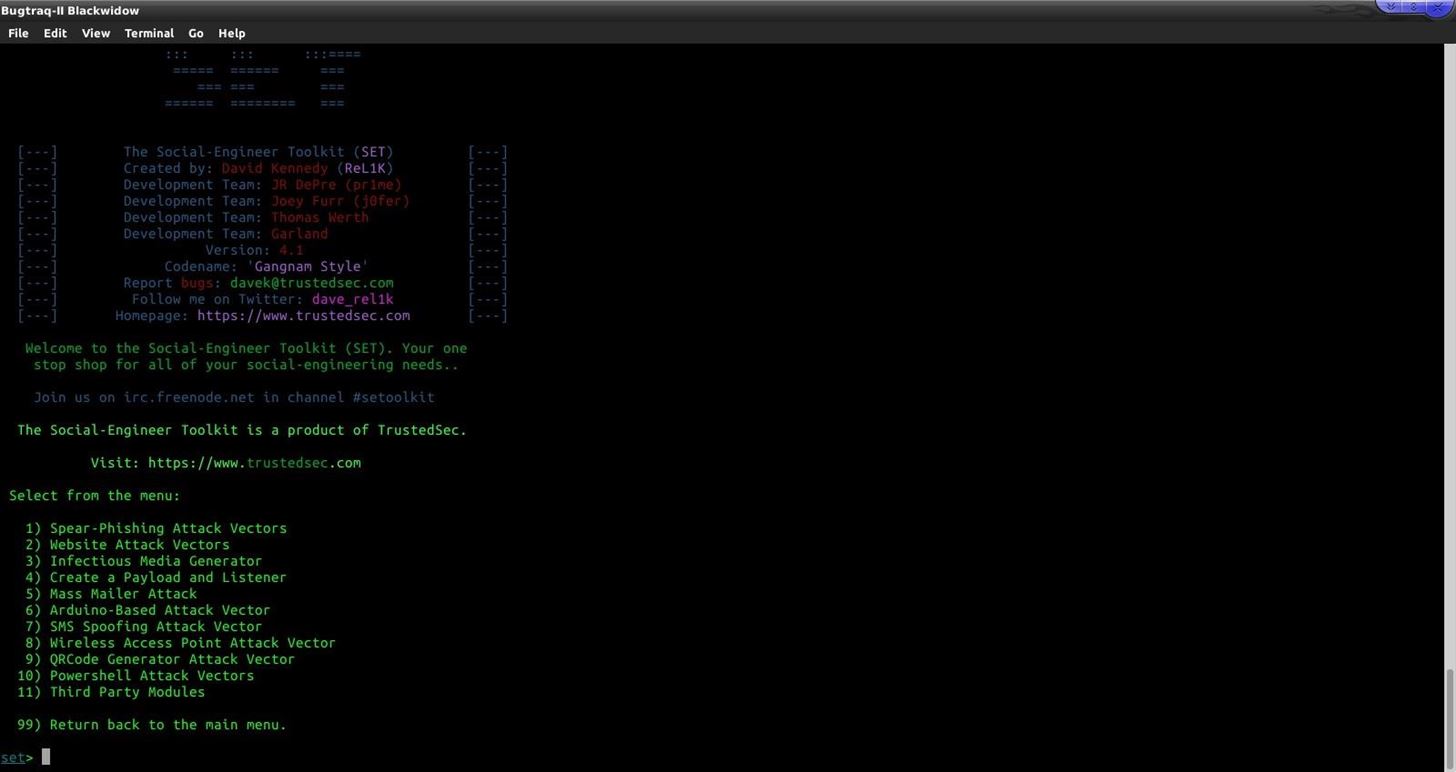
Now there are numerous of things here so let's look into that!
Spear-Phishing Attack Vectors
This tool allows you to send e-mails with a malicious file as payload.
Website Attack Vectors
This tool allows you to create a malicious website link.
Infectious Media Generator
This tool creates a payload and a .ini file for a usb,cd or dvd injection.
Create a Payload and Listener
Straightforward just creates a .exe file and opens a listener.
Mass Mailer Attack
This tool will send e-mails to the target.
Arduino-Based Attack Vector
For use with a "teensy usb."
SMS Spoofing Attack Vector
With this tool you'll be able to craft sms messages and send them.
Wireless Access Point Attack Vector
Should be straightforward.
QRCode Generator Attack Vector
Generates a QRCode to a specific URL.
Powershell Attack Vectors
This will allow you to use Powershell exploits (powershell is available on windows vista and above.)
Third Party Modules
Will allow you to browse for more add-ons.
Step 1: Getting Started!
I won't create a whole tutorial about the different options available in SET because it's just to much. Also SET is pretty straightforward. For example, in metasploit you'll need to use set RHOST:xxx.xxx.xxx.xxx. SET just asks: What is the remote host? ==> xxx.xxx.xxx.xxx
So go ahead and try to social engineer someone, and i hope this helps.
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























9 Comments
Is SET already installed in BugTraq & backtrack if so from where to open it ?????
Well i'm not sure if it's installed on Backtrack. If you'r running bugtraq you should go to pentesting and it should be there!
Th3skYf0x
I had a small problem with bugtraq as Firefox and some other stuff was in Spanish i couldn't understand what i read.
Hmmm....thanks :-)
It is definitely installed on Kali.
too
:-P
@Apparatus 39 - Thank you that was bugging me also. (see what I did there?) LOL
PLEASE HELP
I'm running Kali linux in virtual box on Windows 10;
Tried creating a copy of Facebook and got this error:
"python openssl is not detected or pem file not found note that ssl compatibility will be affected"
@William Kern - It appears you are missing a PEM file, which is a specially encoded certificate. Honestly, I find that trying to run hacks in a VM are nothing but trouble. Stop relying on Winblows, take a leap of faith (in yourself) and stop running Kali in a VM on top of Winblows. You would be better off to install Kali or Parrot Security and run Winblows in a VM if you REALLY need mycockisoft er I mean microsoft. hehehe =)
Share Your Thoughts