This is a quick and easy method for receiving the backend IP (1) of a server who is hidden behind a proxy (2) or a firewall (3).
Requiring the following:
- Attacker can use a browser
- Or Attacker have a basic knowledge of PHP (4)
- A page who provides the "Upload through URL" option
Step 1: Using the Easy Method
In this case the attacker only need a working browser and have to visit the following page:
Then press in the window "Invisible logger" the button "Generate logger"
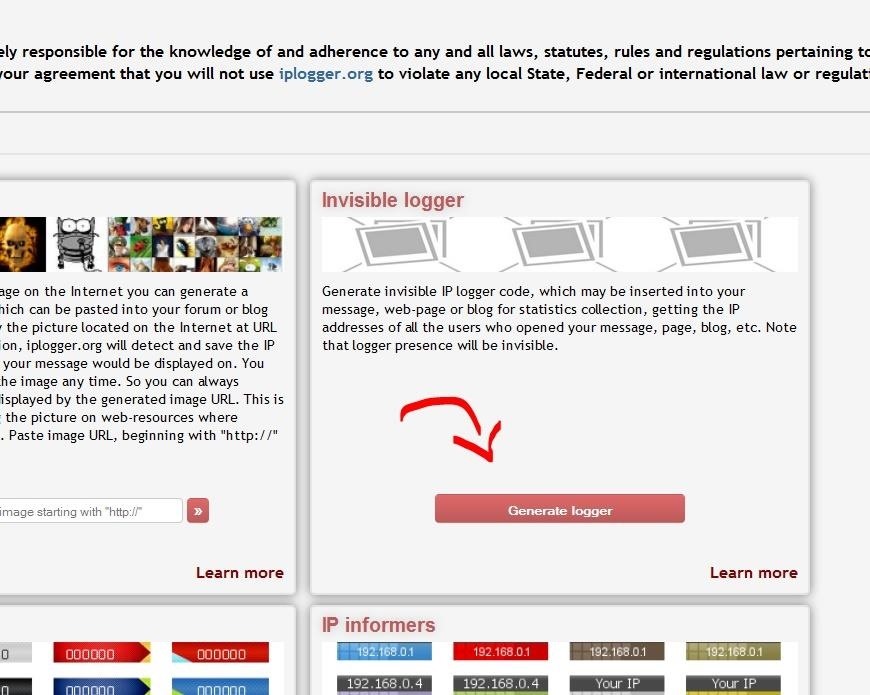
Now we will be redirected to a new page. URL would be for example:
http://iplogger.org/statistics/id=SOME_RANDOM_ID/
all we need is copying the "No BB Code" link out of it
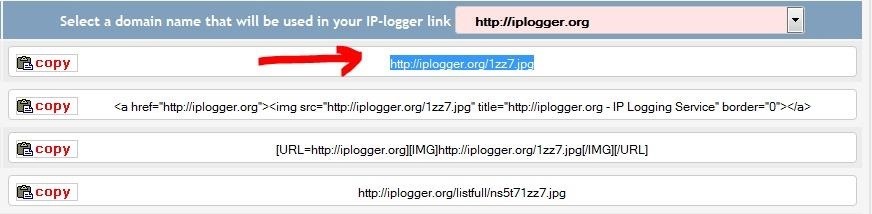
and paste it into the "Upload via URL" form
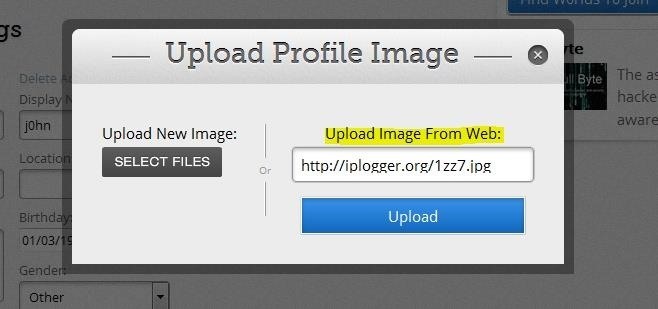
After our upload finished, we can visit our generated link again and voila backend IP dropped:

After a quick check:
- Original IP: 8.26.65.101| USA | Lightcrest LLC
- Backend IP: 8.26.64.82 | USA | Lightcrest LLC
we are finished!
Of course in this case we dont know if its the true backend IP of wonderhowto it was just an example.
Step 2: Using Our Own Script
Many skidforums blacklistening the domain of the script shown above. But with basic skills of PHP and simple knowledge of rewrite rules we can build and spoof our own IP logger. for example:
.htaccess (5)
RewriteEngine on
RewriteRule ^image.png$ iplogger.php
iplogger.php
http://0bin.net/paste/Y5hAcnbJY8dJPiTT#Yk9OrKPqqDGwT3OZwbe6EHtxD13g8b5nCASlMZW50d4
Explanation
The server is fetching our "image" from the URL we provided and saving it to a temporary cache. Thats how we reiving the true IP address of the server who is working with the image.
Glossary
(1) https://en.wikipedia.org/wiki/Firewall_%28computing%29
(2) https://en.wikipedia.org/wiki/IP_address
(3) https://en.wikipedia.org/wiki/Proxy_server
(4) https://en.wikipedia.org/wiki/PHP
(5) https://en.wikipedia.org/wiki/.htaccess
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.






















3 Comments
Really good tutorial, very creative and useful! I would have thought that the proxy would intercept all the traffic inbound and outbound but I guess not.
Cheers,
Washu
i can't understand what's the point, use nslookup or dig,we can get many information.
In my experience some webservers have visible backend IP addresses with a quick traceroute when using the TCP protocol (to evade most HTTP-based WAF) at port 80. Theoretically trying out port 443 and 53 might also help. The default traceroute request system gets caught by even the simplest of firewalls.
try:
$ traceroute -T <target IP address>
$ traceroute -T --port=<port> <target IP address>
I'm not sure, but maybe you can get lucky if you use port 22 or 23 and find a telnet or ssh service opened up. From there you might be able to bruteforce the credentials with a program of your choice (like Hydra), and bam, you're in.
Share Your Thoughts